Table of Content
The multiple attack methods used by hacktivist teams are resulting in an enormous monetary loss for individuals, enterprises, and governments. Hence, deployment of DDoS protection and mitigation software in various industries is rising. The major aim of DDOS attack is to halt the progress of any on-line administrative application, which is accessed by millions of users, making it inconceivable to use. The attack targets a wide range of network sources, which include web sites, servers, and banks .

In some cases, a well-configured cache — at the community or software stage — can return knowledge previously processed and unchanged. After all, the quickest processing potential is the processing you don't have to perform. Distributed denial of service attack is doubtless considered one of the forms of DOS attacks that aim to limit the availability of companies to end-users. There are quite a few ways a DDOS attack can restrict the providers to the consumer.
What Is Ddos Mitigation?
To deny the availability, a malicious attacker sends spoofed requests to open DNS resolvers that allow recursion. There are hundreds of thousands of open DNS resolvers on the Internet including many home gateways. The open DNS resolver processes these requests as valid after which returns the DNS replies to the spoofed recipient (i.e., the victim).
With this, each division in an organization shall be provided with its personal native space network. Pro-Russian hackers, in the meantime, have claimed accountability or been blamed for assaults on websites and infrastructure within the likes of Lithuania, Norway and the United States this year. Then, I’ll clarify how to check out whether or not you bought attacked utilizing Wireshark. I’ll then show how one can slim your environment’s DDoS API attack surface. Players within the international DDoS Protection and Mitigation Security Market focus on increasing their world attain through varied strategies, similar to; partnerships, collaborations, and partnerships.
Mitigating Ddos: Demystifying Distributed Denial-of-service Assaults
A distributed denial of service attack is a flood of malicious web traffic aimed toward a particular website, service, server or IoT gadget to take it offline. This assault is the equivalent of a clogged drain where nothing can get via the blockage. In order to guard your network and applications from cyber-attacks, it could be very important develop an incident response plan that particulars various applied sciences and protocols needed to protect from DDoS assaults.

Virtually any company—or any virtual company—may now be targets, from cloud suppliers and e-commerce portals to monetary brokerages and the Ubers of the world. A regex match rule statement instructs AWS WAF to match a request part in opposition to a single common expression . A net request matches the statement if the request element matches the regex that you just specify.
System Software Program Requirement Specification
Cost safety to safeguard in opposition to scaling costs resulting from DDoS-related utilization spikes. Protection towards Layer 7 DDoS assaults including AWS WAF at no extra value. All AWS customers profit from the automated protections of AWS Shield Standard, at no additional cost. Experiment and find out about DDoS protection on AWS with step-by-step tutorials. Your account will be throughout the AWS Free Tier, which allows you to gain free, hands-on experience with the AWS platform, products, and companies. If you need a Carrier-Grade NAT and you need to protect NAT addresses, you can steer toward Thunder Threat Protection System by A10.
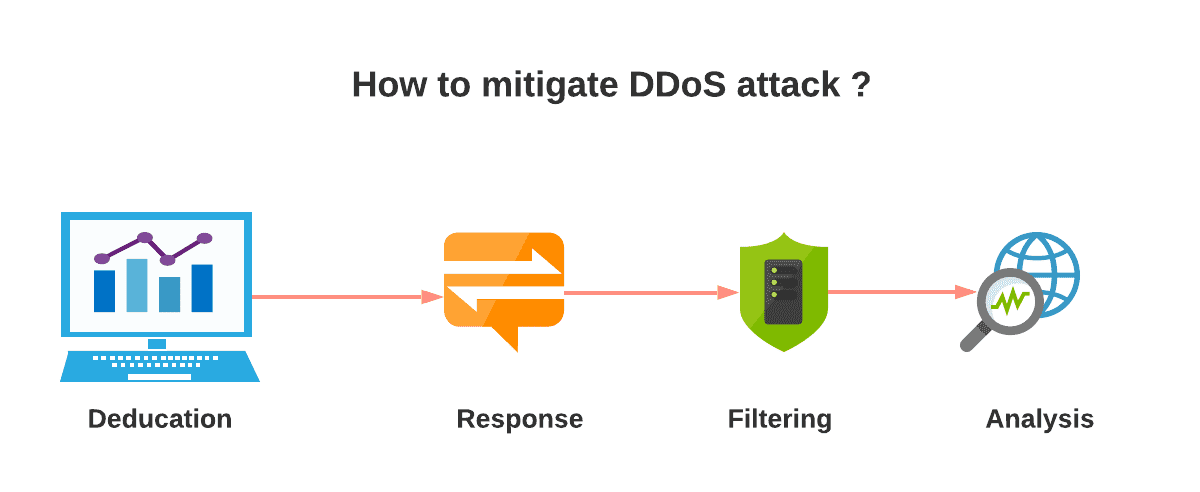
Often, attackers make use of DDoS attacks to extort businesses in an analogous way to ransomware assaults. Here, cyber-criminals flood a victim’s servers and networks with requests, crippling their operations and then demanding money to end the foray. DDoS assaults are widespread cybersecurity threats that may deliver down sites, purposes, and servers by flooding them with junk traffic. This flood of data requests, packets, or queries turns into so overwhelming that the targeted host is not able to process any more knowledge, rendering it unavailable to respectable customers. Additionally, some attacks could exploit vulnerabilities or insecure options to redirect responses to queries to amplify the attack. One of the first methods for mitigating DDoS assaults is to reduce the surface area that may be attacked, limiting attackers' choices and permitting you to construct protections in a single location.
This routing technique is configured in a network to ahead all the malicious and unwanted visitors to a null level, from the place it cannot be forwarded further and dropped. This mechanism is not used very frequently, as it consumes excessive volume of RAM, processing power and bandwidth. To configure this routing, a static route is enabled on the routers deployed in the community. "The bank's technological infrastructure is underneath an unprecedented cyber assault from overseas," VTB stated in an announcement. "The largest not only this year, but in the whole time the financial institution has operated."

When there is one central server, it's simpler to overwhelm it with traffic. When requests from the attack are distributed throughout a decentralized blockchain, a DDoS assault is much less more doubtless to create enough site visitors to close down a whole chain. A Distributed Denial of Service attack is a type of cyberattack where a hacker overwhelms a server with artificial site visitors, making it difficult or inconceivable for regular users to visit the site. Normally, your ability to access a website is like driving down a highway – there are different cars on the street, however they don’t stop you from getting the place you are going.
Proof that mitigation works as promised can also impact compliance and cyber insurance coverage premiums. Select the online ACL, then choose Regular rule, create a String Match rule. A geo-match match assertion that specifies requests originating within the United States. Select the Web ACL that does not have an RBR outlined, then select Rate-based rule. Whatever the reason, DDoS assaults are on the rise, and it’s extra essential than ever to know how to mitigate DDoS.
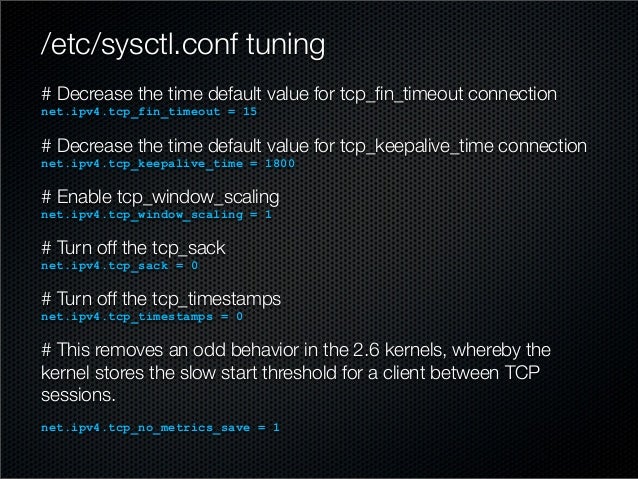
By monitoring these tendencies, if there's an uncommon push of site visitors, it goes to be straightforward to identify and mitigate. Having full visibility of your community and what’s on your network will maintain it protected and less susceptible to assaults exploiting vulnerabilities. Determining and documenting volumes will help mitigate an assault before it takes down your network or earlier than an end consumer even knows something has happened. As a solution supplier, getting ready and protecting companies from cyber threats is one thing CCI Systems does every week. Despite the low barrier of entry, a DDoS attack of this measurement lacks scale, and it'll not be strong enough to take down a bigger target, like a service supplier or operator. DDoS assaults can be categorised based mostly on which layer of the Open Systems Interconnection mannequin they target.
The cybersecurity improvements pioneered by Factom had been succesful sufficient to land Factom multiple government contracts, including with the Department of Homeland Security and the Department of Energy. These contracts speak volumes to the extent of enterprises that belief the design of the blockchain, which is being significantly extra improved underneath Accumulate. During one of these outages, which lasted 17 hours, Solana saw its community traffic and worth diminish. The low cost of transactions on the Solana blockchain, usually an enormous profit, allowed these assaults to happen. Solana can usually course of 65,000 transactions a second, but hackers have been sending upwards of four hundred,000 transactions a second across the chain – inflicting a backup that made normal operations unimaginable.
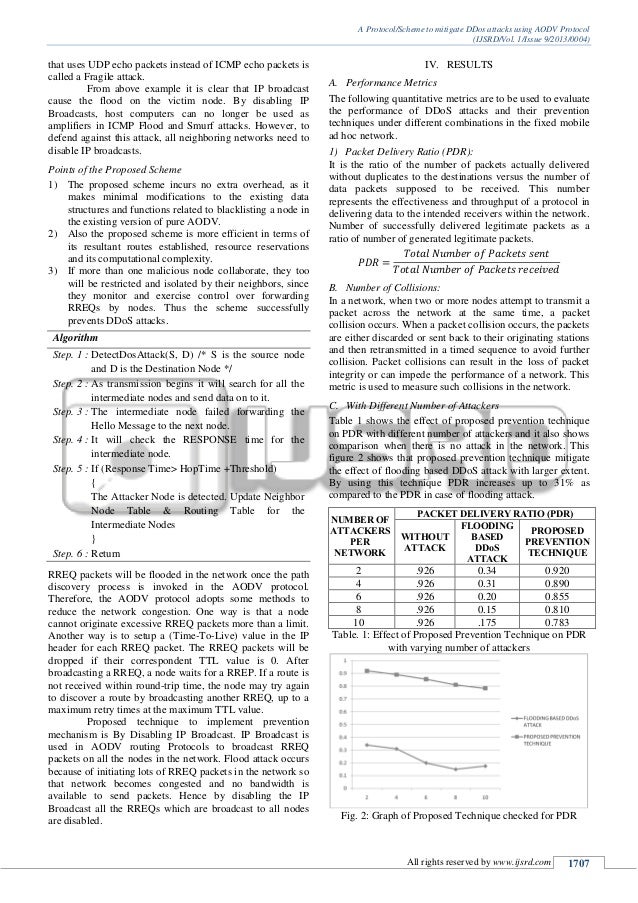

No comments:
Post a Comment